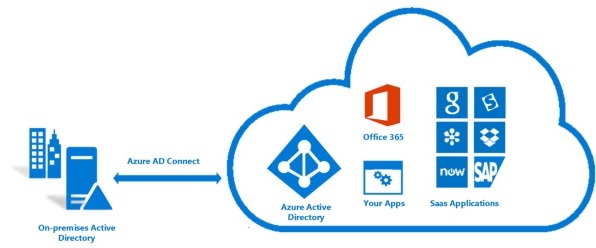
Here after you will find information regarding Azure AD Connect, how it works and how to implement it.
Why use Azure AD Connect?
Integrating your on-premises directories with Azure AD makes your users more productive by providing a common identity for accessing both cloud and on-premises resources. Users and organizations can take advantage of:
- Users can use a single identity to access on-premises applications and cloud services such as Office 365.
- Single tool to provide an easy deployment experience for synchronization and sign-in.
- Provides the newest capabilities for your scenarios. Azure AD Connect replaces older versions of identity integration tools such as DirSync and Azure AD Sync. For more information, see Hybrid Identity directory integration tools comparison.
What’s Azure AD Connect?
Azure AD Connect is the Microsoft tool designed to meet and accomplish your hybrid identity goals. It provides the following features:
- Password hash synchronization – A sign-in method that synchronizes a hash of a users on-premises AD password with Azure AD.
- Pass-through authentication – A sign-in method that allows users to use the same password on-premises and in the cloud, but doesn’t require the additional infrastructure of a federated environment.
- Federation integration – Federation is an optional part of Azure AD Connect and can be used to configure a hybrid environment using an on-premises AD FS infrastructure. It also provides AD FS management capabilities such as certificate renewal and additional AD FS server deployments.
- Synchronization – Responsible for creating users, groups, and other objects. As well as, making sure identity information for your on-premises users and groups is matching the cloud. This synchronization also includes password hashes.
- Health Monitoring – Azure AD Connect Health can provide robust monitoring and provide a central location in the Azure portal to view this activity.
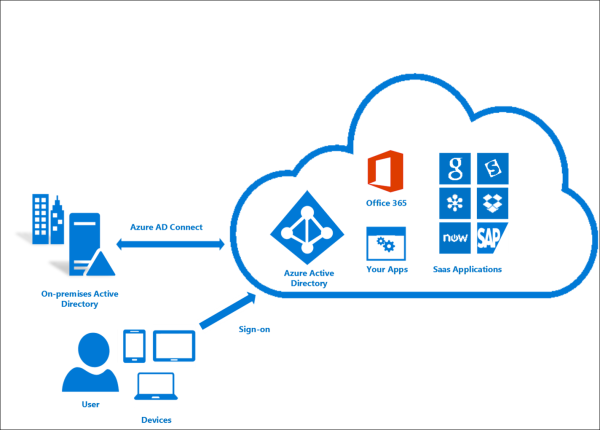
Prerequisites
Azure AD
- An Azure AD tenant. You get one with an Azure free trial. You can use one of the following portals to manage Azure AD Connect:
- The Azure portal.
- The Office portal.
- Add and verify the domain you plan to use in Azure AD. For example, if you plan to use contoso.com for your users then make sure this domain has been verified and you are not only using the contoso.onmicrosoft.com default domain.

- An Azure AD tenant allows by default 50k objects. When you verify your domain, the limit is increased to 300k objects. If you need even more objects in Azure AD, then you need to open a support case to have the limit increased even further. If you need more than 500k objects, then you need a license, such as Office 365, Azure AD Basic, Azure AD Premium, or Enterprise Mobility and Security.
Prepare your on-premises data
- Use IdFix to identify errors such as duplicates and formatting problems in your directory before you synchronize to Azure AD and Office 365.
Blog article regarding IdFix can be found here
- Review optional sync features you can enable in Azure AD and evaluate which features you should enable.
On-premises Active Directory
- The AD schema version and forest functional level must be Windows Server 2003 or later. The domain controllers can run any version as long as the schema and forest level requirements are met.
- If you plan to use the feature password writeback, then the Domain Controllers must be on Windows Server 2008 R2 or later.
- The domain controller used by Azure AD must be writable. It is not supported to use a RODC (read-only domain controller) and Azure AD Connect does not follow any write redirects.
- It is not supported to use on-premises forests/domains using “dotted” (name contains a period “.”) NetBios names.
- It is recommended to enable the Active Directory recycle bin.
Azure AD Connect server
- Azure AD Connect cannot be installed on Small Business Server or Windows Server Essentials before 2019 (Windows Server Essentials 2019 is supported). The server must be using Windows Server standard or better.
- Installing Azure AD Connect on a Domain Controller is not recommended due to security practices and more restrictive settings that can prevent Azure AD Connect from installing correctly.
- The Azure AD Connect server must have a full GUI installed. It is not supported to install on server core.
- Azure AD Connect must be installed on Windows Server 2008 R2 or later. This server must be domain joined and may be a domain controller or a member server.
- If you install Azure AD Connect on Windows Server 2008 R2, then make sure to apply the latest hotfixes from Windows Update. The installation is not able to start with an unpatched server.
- If you plan to use the feature password synchronization, then the Azure AD Connect server must be on Windows Server 2008 R2 SP1 or later.
- If you plan to use a group managed service account, then the Azure AD Connect server must be on Windows Server 2012 or later.
- The Azure AD Connect server must have .NET Framework 4.5.1 or later and Microsoft PowerShell 3.0 or later installed.
- The Azure AD Connect server must not have PowerShell Transcription Group Policy enabled.
- If Active Directory Federation Services is being deployed, the servers where AD FS or Web Application Proxy are installed must be Windows Server 2012 R2 or later. Windows remote management must be enabled on these servers for remote installation.
- If Active Directory Federation Services is being deployed, you need SSL Certificates.
- If Active Directory Federation Services is being deployed, then you need to configure name resolution.
- If your global administrators have MFA enabled, then the URL https://secure.aadcdn.microsoftonline-p.com must be in the trusted sites list. You are prompted to add this site to the trusted sites list when you are prompted for an MFA challenge and it has not added before. You can use Internet Explorer to add it to your trusted sites.
- Microsoft recommends hardening your Azure AD Connect server to decrease the security attack surface for this critical component of your IT environment. Following the recommendations below will decrease the security risks to your organization.
- Deploy Azure AD Connect on a domain joined server and restrict administrative access to domain administrators or other tightly controlled security groups.
SQL Server used by Azure AD Connect
- Azure AD Connect requires a SQL Server database to store identity data. By default a SQL Server 2012 Express LocalDB (a light version of SQL Server Express) is installed. SQL Server Express has a 10GB size limit that enables you to manage approximately 100,000 objects. If you need to manage a higher volume of directory objects, you need to point the installation wizard to a different installation of SQL Server. The type of SQL Server installation can impact the performance of Azure AD Connect.
- If you use a different installation of SQL Server, then these requirements apply:
- Azure AD Connect supports all versions of Microsoft SQL Server from 2008 R2 (with latest Service Pack) to SQL Server 2019. Microsoft Azure SQL Database is not supported as a database.
- You must use a case-insensitive SQL collation. These collations are identified with a _CI_ in their name. It is not supported to use a case-sensitive collation, identified by _CS_ in their name.
- You can only have one sync engine per SQL instance. It is not supported to share a SQL instance with FIM/MIM Sync, DirSync, or Azure AD Sync.
Accounts
- An Azure AD Global Administrator account for the Azure AD tenant you wish to integrate with. This account must be a school or organization account and cannot be a Microsoft account.
- If you use express settings or upgrade from DirSync, then you must have an Enterprise Administrator account for your on-premises Active Directory.
- Accounts in Active Directory if you use the custom settings installation path or an Enterprise Administrator account for your on-premises Active Directory.
Connectivity
- The Azure AD Connect server needs DNS resolution for both intranet and internet. The DNS server must be able to resolve names both to your on-premises Active Directory and the Azure AD endpoints.
- If you have firewalls on your Intranet and you need to open ports between the Azure AD Connect servers and your domain controllers, then see Azure AD Connect Ports for more information.
- If your proxy or firewall limit which URLs can be accessed, then the URLs documented in Office 365 URLs and IP address rangesmust be opened.
- If you are using the Microsoft Cloud in Germany or the Microsoft Azure Government cloud, then see Azure AD Connect sync service instances considerations for URLs.
- Azure AD Connect (version 1.1.614.0 and after) by default uses TLS 1.2 for encrypting communication between the sync engine and Azure AD. If TLS 1.2 isn’t available on the underlying operating system, Azure AD Connect incrementally falls back to older protocols (TLS 1.1 and TLS 1.0).
- Prior to version 1.1.614.0, Azure AD Connect by default uses TLS 1.0 for encrypting communication between the sync engine and Azure AD. To change to TLS 1.2, follow the steps in Enable TLS 1.2 for Azure AD Connect.
- If you are using an outbound proxy for connecting to the Internet, the following setting in the C:\Windows\Microsoft.NET\Framework64\v4.0.30319\Config\machine.config file must be added for the installation wizard and Azure AD Connect sync to be able to connect to the Internet and Azure AD. This text must be entered at the bottom of the file. In this code, <PROXYADDRESS> represents the actual proxy IP address or host name.
In the next article we will see the step-by-step installation and configuration