Citrix has finally released XMS version 10.7.0 binary 😉
Can be download here using your MyCitrix account.
Here after some more information:
Important
After an upgrade to XenMobile 10.7:
If functionality involving outgoing connections stop working, and you haven’t changed your connection configuration, check the XenMobile Server log for errors, such as the following: Unable to connect to the VPP Server: Host name ‘192.0.2.0’ does not match the certificate subject provided by the peer.
If you receive the certificate validation error, disable hostname verification on XenMobile Server. By default, hostname verification is enabled on outgoing connections except for the Microsoft PKI server. If hostname verification breaks your deployment, change the server property disable.hostname.verification to true. The default value of this property is false.
XenMobile Server 10.7 includes the following new features:
- Integrate with Apple Education features
- Deploy iBooks to iOS devices
- BitLocker device policy
- New restrictions for supervised devices running iOS 10.3 and later
- Restart or shut down a supervised iOS device
- Locate or ring a supervised iOS device that’s in lost mode
- Enhanced Android for Work support
- More macros for enrollment templates
- Other improvements
- Public REST API changes
Important
TouchDown by Symantec reached End of Life on July 3, 2017, with End of Standard Support, End of Extended Support, and End of Support Life on July 2, 2018. For more information, see the Symantec support article, TouchDown End-of-Life, End-of-Availability, and End-of-Support announcement.
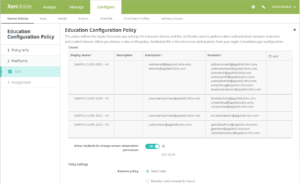
Integrate with Apple Education features
You can use XenMobile Server as your mobile device management (MDM) solution in an environment that uses Apple Education. XenMobile supports the Apple Education enhancements introduced in iOS 9.3, including Apple School Manager and Classroom app for iPad. The new XenMobile Education Configuration device policy configures instructor and student devices for use with Apple Education.
The following video provides a quick tour of the changes you make to Apple School Manager and XenMobile Server.
Citrix XenMobile Education Configuration: Integrate Apple Education features with XenMobile
https://youtube.com/watch?v=0IemxkP7Meg
You provide preconfigured and supervised iPads to instructors and students. That configuration includes:
- Apple School Manager DEP enrollment in XenMobile
- A Managed Apple ID account configured with a new password
- Required VPP apps and iBooks
For details about integrating with Apple Education features, see Integrate with Apple Education features and Education Configuration device policy.
Deploy iBooks to iOS devices
You can use XenMobile to deploy iBooks that you obtain through the Apple Volume Purchase Program (VPP). After you configure a VPP account in XenMobile, your purchased and free books appear in Configure > Media. From the Media pages, you configure iBooks for deployment to iOS devices by choosing delivery groups and specifying deployment rules.
The first time that a user receives an iBook and accepts the VPP license, deployed books install on the device. The books appear in the Apple iBook app. You can’t disassociate the book license from the user or remove the book from the device. XenMobile installs iBooks as required media. If a user deletes an installed book from their device, the book remains in the iBook app, ready for download.
Prerequisites
- iOS devices (minimum version iOS 8)
- Configure iOS VPP in XenMobile, as described in iOS Volume Purchase Plan.
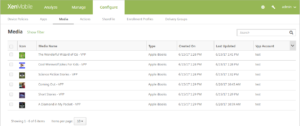
Configure iBooks
iBooks obtained through VPP appear on the Configure > Media page. For more information, see Add media.
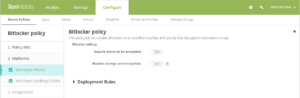
BitLocker device policy
Windows 10 Enterprise includes a disk encryption feature called BitLocker, which provides extra file and system protections against unauthorized access of a lost or stolen device. For more protection, you can use BitLocker with Trusted Platform Module (TPM) chips, version 1.2 or later. A TPM chip handles cryptographic operations and generates, stores, and limits the use of cryptographic keys.
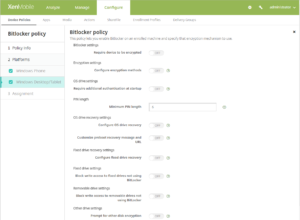
Starting with Windows 10, build 1703, MDM policies can control BitLocker. You use the BitLocker device policy in XenMobile to configure the settings available in the BitLocker wizard on Windows 10 devices. For example, on a device with BitLocker enabled, BitLocker can prompt users for:
- How they want to unlock their drive at startup
- How to back up their recovery key
- How to unlock a fixed drive.
BitLocker device policy setting also configure whether to:
- Enable BitLocker on devices without a TPM chip.
- Show recovery options in the BitLocker interface.
- Deny write access to a fixed or removable drive when BitLocker isn’t enabled.
For more information, see BitLocker device policy.
New restrictions for supervised devices running iOS 10.3 and later
Restrictions allow you to prevent users from performing certain actions on their devices and are implemented through device policies.
The following restrictions are now available for devices running iOS 10.3 and later, in supervised mode:
- Allow Dictation: Supervised only. If this restriction is set to OFF, dictation input is not allowed. The default setting is ON. For iOS 10.3 and later.
- Force WiFi white listing: Optional. Supervised only. If this restriction is set to ON, the device can join Wi-Fi networks only when they were set up through a configuration profile. The default setting is OFF. For iOS 10.3 and later.
To set these restrictions:
- In the XenMobile console, select Configure > Device Policies. The Device Policies page appears.
- Select Add. The Add a New Policy page appears.
- Click Restrictions. The restrictions Policy information
- page appears.
In the Policy Information pane, type the following information:
Policy Name: Type a descriptive name for the policy.
Description: Type an optional description of the policy. - Click Next. The Policy Platforms page appears.
- Select iOS.
- Click Next until the page showing the Single App bundle ID section appears. Set the restrictions.
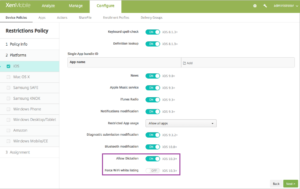
For more information on setting restrictions, see Restrictions device policy.
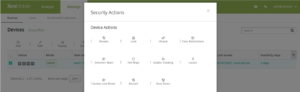
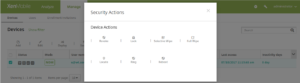
Restart or shut down a supervised iOS device
You can use security actions to restart or shut down a supervised iOS device (minimum version 10.3). Go to Manage > Devices, select the device, click Security, and then click Restart or Shut Down.
A device restarts immediately when it receives the Restart command. Passcode-locked iOS devices don’t rejoin WiFi networks after restarting, so they might not communicate with the server. A device shuts down immediately when it receives the Shut Down command.
Locate or ring a supervised iOS device that’s in lost mode
After you place a supervised iOS device in lost mode, you can use security actions to locate or ring the device. A “ring” is the lost mode sound that Apple defines for the device.
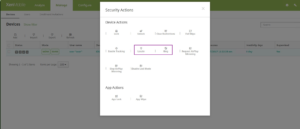
- To locate a device that’s in lost mode:
Go to Manage > Devices, select the device, click Security, and then click Locate. The Device details page provides a status of the location request.
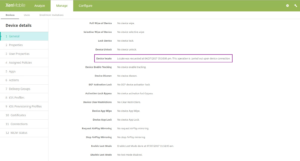
If the device is located, the Device details page includes a map.
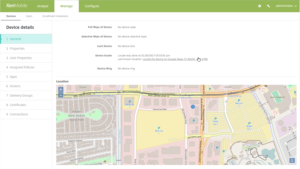
- To ring a device that’s in lost mode (minimum version iOS 10.3):
Go to Manage > Devices, select the device, click Security, and then click Ring. The next time that the device connects, it rings. To stop the ring, the user clicks the power button. To stop the ring from the XenMobile console, use the Disable Lost Mode security action.Enhanced Android for Work support
XenMobile now provides a simple way to set up Android for Work for your organization. Using XenMobile Management Tools, you bind XenMobile as your enterprise mobility management provider through Google Play and create an enterprise for Android for Work.
Note
G Suite customers, use the legacy Android for Work settings to configure legacy Android for Work, as described in the Android for Work article. Click legacy Android for Work in the Android for Work page in XenMobile Settings.
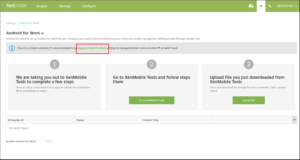
You need:
- Your Citrix account credentials to sign in to XenMobile Tools
- Your corporate Google ID credentials to sign in to Google Play
For more information, see Android for Work.
Support for Device Health Attestation (DHA) on-premises
You can now enable Device Health Attestation (DHA) for Windows 10 mobile devices through an on-premises Windows server. Previously, DHA for XenMobile may be enabled only through Microsoft Cloud.
To enable DHA on-premises, you first configure a DHA server. Then you create a XenMobile Server policy to enable the on-premises DHA service.
To configure a DHA, you need a machine running Windows Server 2016 Technical Preview 5 or later. You install DHA as a server role. For instructions, see this Microsoft TechNet article, Device Health Attestation.
To the XenMobile Server policy to enable the on-premises DHA service:
1. In the XenMobile console, click Configure > Device Policies. The Device Policies page appears.
2. If you have already created a policy to enable DHA through Microsoft Cloud, skip to step 8.
3. Click Add to add a new policy. The Add a New Policy dialog box appears.
4. Click More, and then under Custom, click Device Health Attestation policy. The Device Health Attestation Policy information page appears.
5. In the Policy Information pane, enter the following information:
Policy Name: Type a descriptive name for the policy.
Description: Type an optional description of the policy.
6. Click Next. The Policy Platforms page appears.
7. Under Platforms, select the platforms you want to add. If you are only configuring for one platform, clear the others.
8. For each platform that you choose:
a. Set Enable Device Health Attestation to ON.
b. Set Configure On-prem Health Attestation Service to ON.
c. In On-prem DHA Service FQDN, enter the fully qualified domain name of the DHA server you set up.
d. In On-prem DHA API version, choose the version choose the version of the DHA service installed on the DHA server.
9. Configure deployment rules and choose delivery groups.

To confirm that the policy has been pushed to a Windows 10 Mobile device:
1. In the XenMobile console, click Manage > Device.
2. Select the device.
3. Select Properties.
4. Scroll down to see “Windows Device Health Attestation.”
More macros for enrollment templates
You can use these new macros when creating enrollment templates for device enrollment invitations:
${enrollment.urls}
${enrollment.ios.url}
${enrollment.macos.url}
${enrollment.android.url}
${enrollment.ios.platform}
${enrollment.macos.platform}
${enrollment.android.platform}
${enrollment.agent}
These macros allow you to create enrollment templates that contain enrollment URLs for multiple device platforms.
This example shows how to create a notification that includes enrollment URLs for multiple device platforms. The macro for the Message is:
${enrollment.urls}
These examples show how to create messages for notifications that prompt the users to click the enrollment URL for their device platforms:
Example 1:
To enroll, please click the link below that applies to your device platform:
${enrollment.ios.platform} – ${enrollment.ios.url}
${enrollment.macos.platform} – ${enrollment.macos.url}
${enrollment.android.platform} – ${enrollment.android.url}
Example 2:
To enroll an iOS device, click the link ${enrollment.ios.url}.
To enroll a macOS device, click the link ${enrollment.macos.url}.
To enroll an Android device, click the link ${enrollment.android.url}.
Other improvements
- The XenMobile console and the Self Help Portal are now available in Spanish.
- XenMobile now reports the Security patch level for Android devices. You can view the Security patch level on the Manage > Devices page and in Device details. You can also use Configure > Actions to create an action that the security patch level triggers.
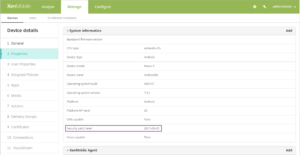
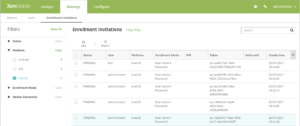
- Filter enrollment invitations by macOS. The Platform filter for Manage > Enrollment Invitations now includes macOS.
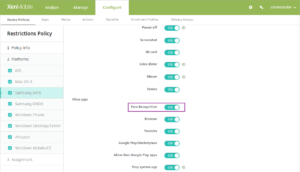
- Restrictions policy setting to block users from using face recognition to unlock Samsung Galaxy S8+ devices. The Restrictions device policy for Samsung SAFE now includes the setting, Face Recognition. To block use of face recognition to unlock device access, go to Configure > Device Policies and edit the Restrictions policy to set Face Recognition to Off.
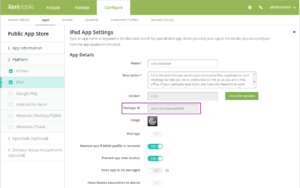
- Required macOS VPP apps now supported. You can now deploy macOS VPP apps as required apps for both Active Directory and local users. You can view macOS VPP apps in Configure > Apps, where you can filter the apps by macOS VPP. On that page, the Store Configuration section doesn’t appear for macOS VPP apps because there is no Secure Hub for macOS. In Manage > Devices, the User Properties include Retire VPP account for macOS VPP accounts.
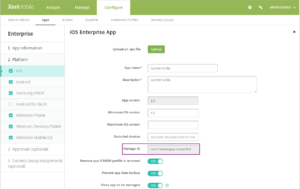
- Configure > Apps now shows the Package ID for public app store apps and enterprise apps
- Alphabetized resource lists for delivery groups. In Configure > Delivery Groups, all resource lists and search results appear in alphabetical order.
- On the Manage > Devices and Manage > Users pages, dates now appear in the 24-hour format, dd/mm/yyyy hh:mm:ss. Dates reflect the local time zone for devices and users.
- The VPN policy for iOS devices now has a per-app VPN option for iKEv2 type VPN policies. iOS 9.0 and later devices support per-app VPN for iKEv2 connections. The per-app VPN Enable per-app VPN options are:
Enable per-app VPN
On-demand match app enabled
Safari domains
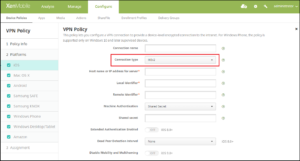
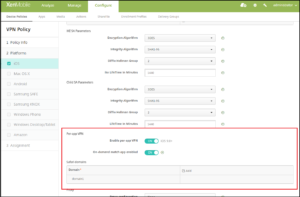
Under the “iOS” section, add to the iKEv2 connection type section:
Enable per-app VPN: Select whether to enable per-app VPN. The default is OFF. Available only on iOS 9.0 and later.
On-demand match app enabled: Select whether per-app VPN connections are triggered automatically when apps linked to the per-app VPN service initiate network communication. The default is OFF.
Safari domains: Click Add to add a Safari domain name.
- Wipe code for macOS devices shown in the XenMobile console. macOS devices require the user to enter a PIN code after the device has been wiped. If the user does not remember this code, you can now look up the wipe code in the Manage > Device details page.
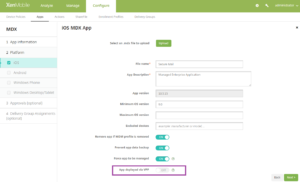
- When you use VPP to deploy an MDX app, the Secure Hub store now shows only the VPP instance of the app. Previously, both the VPP and MDX apps appeared in the store. This change prevents end users from installing the MDX version of the app, which requires the user to have an iTunes account. When you add an MDX app, there is a new setting, App deployed via VPP. Change that setting to ON if you plan to deploy the app by using VPP.
- Improved performance when importing many VPP licenses. This optimization uses multi-threading. A new XenMobile Server property, MaxNumberOfWorker, defaults to 3 (threads). If you need further optimization, you can increase the number of threads. However, with a larger number of threads, such as 6, a VPP import results in very high CPU usage.
- In the XenMobile console, all references to Mac OS X, OS X, OSX, MACOSX, and MacOS are now macOS.
- Reboot a Windows 10 device. You can now send a security action, Reboot, to reboot a device. For Windows Tablet and PCs, the message “System will reboot soon” appears and then the reboot occurs in five minutes. For Windows Phone, there is no warning message to users and the reboot occurs after a few minutes.
Public REST API changes
For the device notification REST services, you can now notify a device by using the device ID, without requiring XenMobile to send a token.
When using the XenMobile Public REST API to create enrollment invitations, you can now:
- Specify a custom PIN. If the enrollment mode requires a PIN, you can use a custom PIN instead of the one randomly generated by the XenMobile Server. The PIN length must match the setting configured for the enrollment mode. The PIN length defaults to 8. For example, a request might include: “pin”: “12345678”
- Select multiple platforms. Previously, you could use the REST API to specify only one platform for an enrollment invitation. The “platform” field is deprecated and replaced with “platforms”. For example, a request might include: “platforms”: [“iOS”, “MACOSX”]
The XenMobile Public API for REST Services now includes the following APIs: - Get by Container ID
MDX mobile apps
Enterprise mobile apps
WebLink apps
Web/SaaS apps
Public store apps - Upload app in new or existing container
MDX mobile apps
Enterprise mobile apps - Update platform details inside the container for MDX mobile apps and public store apps
- Add or update app
WebLink apps
Web/SaaS apps
Public store apps - Get all Web/SaaS connectors or get Web/Saas connectors by connector name
- Delete app container
MDX mobile apps
Enterprise mobile apps
WebLink apps
Web/SaaS apps
For details, see XenMobile Public API for REST Services.