The Legacy MAM Mode is possible in 2 ways:
- The user enroll his device by providing the NetScaler Gateway URL instead of the XMS URL
- The user provide the XMS URL and answers No to the question for Enrolling his device
The result his the same, the device will enroll in Legacy MAM Mode.
When Legacy MAM Mode is used, the connection is made only through the NetScaler Gateway, and so manage by the NetScaler Gateway configuration.
Most of the implementation on which I worked in the past are done in a similar way:
The LDAP authentication is configured with a service account for LDAP connections settings and only sAMAccountName or Userprincipalname are used for Server Logon Name Attribute.
The result is that every users members of the domain are able to enroll in Legacy MAM Only.
The fact is that should want to secure this or filter the Access to the Legacy MAM Mode.
Here is some steps to accomplish this:
- Create an Active Directory Security Group named for example: Legacy-MAM-Only.
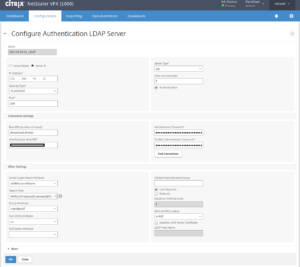
- Add a search filter on your LDAP Configuration on the NetScaler:
- Search Filter: memberOf=CN=Legacy-MAM-Only,CN=Users,DC=arnaud,DC=lab (replace with you own information)
- Group Attribute: memberof
- Sub Attribute Name: cn
That’s it!
The user experience with this configuration will be the following:
User open Secure Hub and provide the XMS FQDN (or his email if autodiscovery is enabled) OR provide the FQDN of the NetScaler Gateway
In the following example we assume that the user use the XMS FQDN
User NOT member of the AD Group:
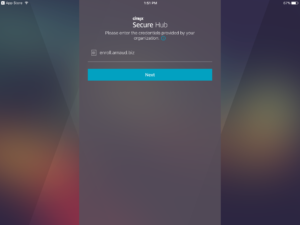
The user tap on Next
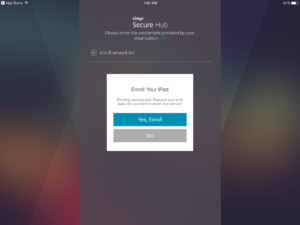
The user tap on No
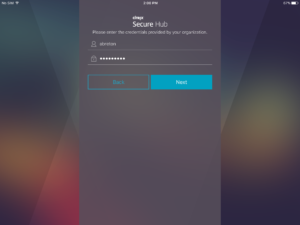
The user provide his credentials and tap on Next
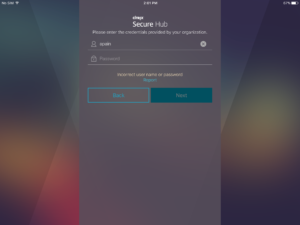
As the user is not member of the Legacy-MAM-only Active Directory group, the message Incorrect user name or password appear (I need to see if this message can me modified on the NetScaler to something like: You are not authorized to connect on legacy MAM only Mode)
User member of the AD Group:
Now, after adding the user to the Active Directory group, after taping on Next
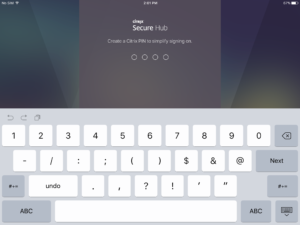
The user is provided to create a WorxPIN, if a policy requesting one exist
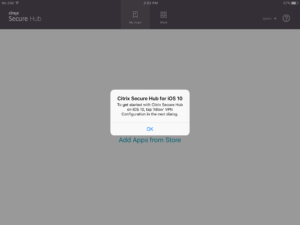
And the user need to Allow VPN configuration
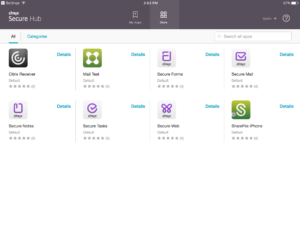
And the Store is accessible
Note: Those information are provided based on my own experience.