
In this article, we will see how to use device compliance policies and conditional access with Intune to make sure that iOS devices can access Exchange Online email only if they’re managed by Intune and use Outlook application.
Create the iOS device compliance policy
Set up an Intune device compliance policy to set the conditions that a device must meet to be considered compliant. For this tutorial, we’ll create a device compliance policy for iOS devices. Compliance policies are platform-specific, so you need a separate compliance policy for each device platform you want to evaluate.
- In Intune, select Device compliance > Policies > Create Policy.

- In Name, enter iOS compliance policy
- In Description, enter iOS compliance policy
- Under Platform, select iOS.

- Select Settings > Email.
- Next to Require mobile devices to have a managed email profile, select Require.
- Select OK.

- Select Device Health. Next to Jailbroken devices, select Block, and then select OK.

- Select System Security and enter Password settings. For this tutorial, select the following recommended settings:
- For Require a password to unlock mobile devices, select Require.
- For Simple passwords, select Block.
- For Minimum password length, enter 4.
- For Required password type, choose Alphanumeric.
- For Maximum minutes after screen lock before password is required, choose Immediately.
- For Password expiration (days), enter 41.
- For Number of previous passwords to prevent reuse, enter 5.
- Select OK

- Select OK again

- Select Create

Create the conditional access policy
Now we’ll create a conditional access policy that requires all device platforms to enroll in Intune and comply with our Intune compliance policy before they can access Exchange Online. We’ll also require the Outlook app for email access. Conditional access policies are configurable in either the Azure AD portal or the Intune portal. Since we’re already in the Intune portal, we’ll create the policy here.
- In Intune, select Conditional access > Policies > New policy.

- In Name, enter Office 365 email Policy.

- Click on Assignments

- Select Users and groups. On the Include tab, select All users, and then select Done.

- Under Assignments, select Cloud apps. Because we want to protect Office 365 Exchange Online email, we’ll select it by following these steps:
- On the Include tab, choose Select apps.
- Choose Select.
- In the applications list, select Office 365 Exchange Online, and then choose Select.
- Select Done.

- Under Assignments, select Conditions > Device platforms.
- Under Configure, select Yes.
- On the Include tab, select All platforms (including unsupported), and then select Done.
- Select Done again.

- Under Assignments, select Conditions > Client apps.
- Under Configure, select Yes.
- Select Mobile apps and desktop clients and Modern authentication clients (which refers to apps like Outlook for iOS and Outlook for Android). Clear all other check boxes.
- Select Done, and then select Done again.

- Under Access controls, select Grant.
- On the Grant pane, select Grant access.
- Select Require device to be marked as compliant.
- Select Require approved client app.
- Under For multiple controls, select Require all the selected controls. This setting ensures that both requirements you selected are enforced when a device tries to access email.
- Choose Select.

- Under Enable policy, select On.
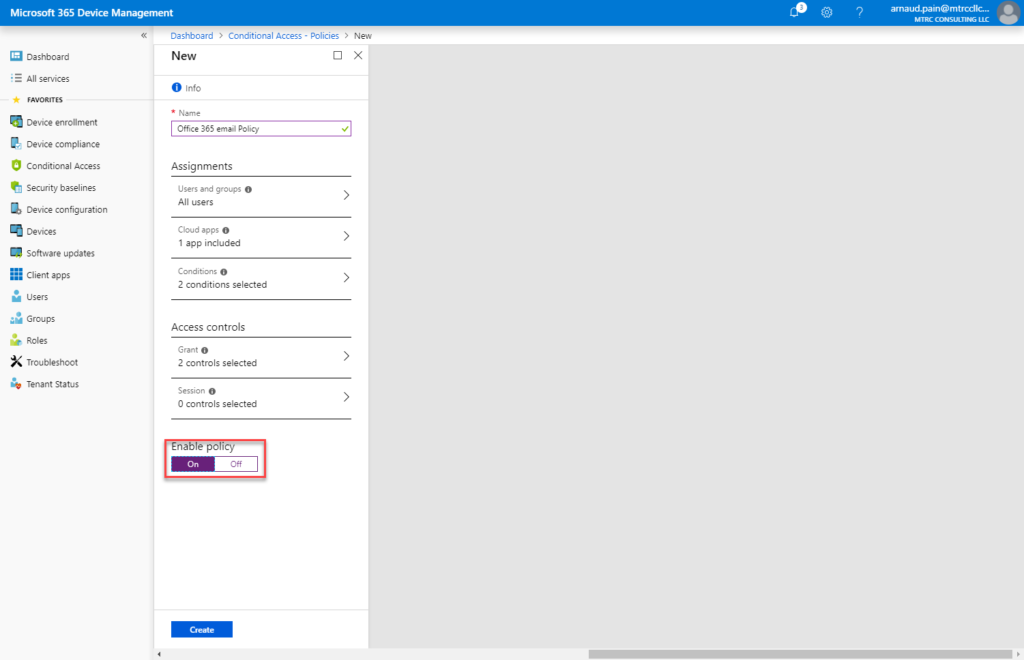
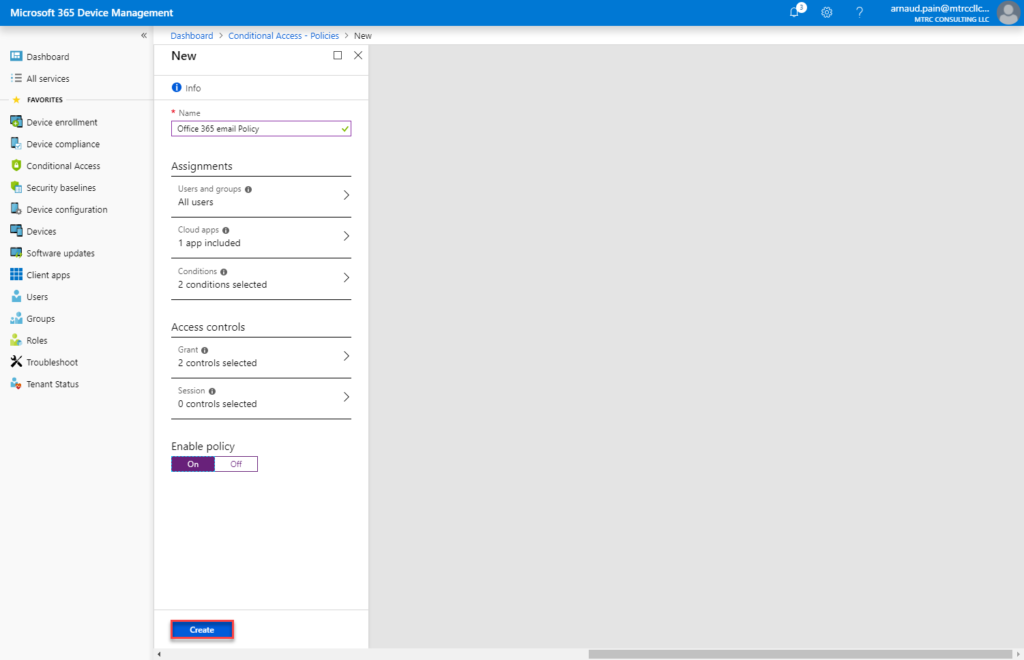
- Select Create.
Try it out
With the policies you’ve created, any iOS device that attempts to sign in to Office 365 email will need to enroll in Intune and use the Outlook mobile app for iOS. To test this scenario on an iOS device, try signing in to Exchange Online using credentials for a user in your test tenant. You’ll be prompted to enroll the device and install the Outlook mobile app.
- To test on an iPad, go to Settings > Passwords & Accounts > Add Account > Exchange.

- Enter the email address for a user in your test tenant, and then press Next.

- Press Sign In.

- Enter the test user’s password, and press Sign in.

- Press Save Password

- As my account is protected with MFA, I am asked to provide a code

- Press Verify

- A message appears that says your device must be managed to access the resource, along with an option to enroll.
Enroll a Device
- Press Enroll Now

- Press GET THE APP

- Press Open

- Press GET

- Once the Application is downloaded press OPEN
- Provide you email and press Go

- Provide your password and press Sign in

- Press Begin

- Press Continue

- Press Continue

- Press Allow

- Press Install

- Press Install

- Press Install

- Press Trust

- Press Done

- Press Open

- Press Done

- You’re presented with the above screen
Now if you restart the Exchange configuration on your device you will have the following message as native email is not authorized

You will need to get Outlook application from public store

Open the application and configure your email

You have access to your email!
Feedback
The configuration is quite simple and the console seems very intuitive.
You have a simple way to secure access to corporate email with just some few mouse click.
My next step will be to integrate Citrix Endpoint Management with Intune, stay tuned for next articles …
