Citrix has announced an early adopter release of XenMobile Server 10.8 Preview 1.
Important: Customer should update their Citrix License server(11.14.x) before updating to the latest version of XenMobile Server 10.8.
Install offline maps on supervised Windows 10 phone devices
Windows 10 phone devices support offline maps. Use the Maps device policy to specify which maps to download to devices. The Microsoft Maps configuration service provider (CSP) currently supports maps of Germany, the United Kingdom, and the United States.
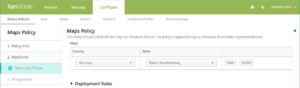
New restrictions for supervised devices running iOS
The following restrictions are now available for iOS devices running in supervised mode. The minimum version supported for each restriction is noted.
- Allow the Classroom app to remotely observe student screens: If this restriction is unselected, an instructor can’t use the Classroom app to observe student screens remotely. The default setting is selected, an instructor can use the Classroom app to observe student screens. The setting for Allow the Classroom app to perform AirPlay and View Screen without prompting determines whether students receive a prompt to give the instructor permission. For supervised devices running iOS 9.3 (minimum version).
- Allow the Classroom app to perform AirPlay and View Screen without prompting: If this restriction is selected, the instructor can perform AirPlay and View Screen on a student device, without prompting for permission. The default setting is unselected. For supervised devices running iOS 10.3 (minimum version).
- Allow the Classroom app to lock to an app and lock the device without prompting: If this restriction is set to On, the Classroom app automatically locks user devices to an app and locks the device, without prompting the users. The default setting is Off. For supervised devices running iOS 11 (minimum version).
- Automatically join the Classroom app classes without prompting: If this restriction is set to On, the Classroom app automatically joins users to classes, without prompting the users. The default setting is Off. For supervised devices running iOS 11 (minimum version).
- Allow AirPrint: If this restriction is set to Off, users can’t print with AirPrint. The default setting is On. When this restriction is On, these extra restrictions appear. For supervised devices running iOS 11 (minimum version).
- Allow storage of AirPrint credentials in Keychain: If this restriction is unselected, the AirPrint user name and password aren’t stored in the Keychain. The default setting is selected. For supervised devices running iOS 11 (minimum version).
- Allow discovery of AirPrint printers by using iBeacons: If this restriction is unselected, iBeacon discovery of AirPrint printers is disabled. Disabling discovery prevents spurious AirPrint Bluetooth beacons from phishing for network traffic. The default setting is selected. For supervised devices running iOS 11 (minimum version).
- Allow AirPrint only to destinations with trusted certificates: If this restriction is selected, users can use AirPrint to print only to destinations with trusted certificates. The default setting is unselected. For supervised devices running iOS 11 (minimum version).
- Adding VPN configurations: If this restriction is set to Off, users can’t create VPN configurations. The default setting is On. For supervised devices running iOS 11 (minimum version).
- Modifying cellular plan settings: If this restriction is set to Off, users can’t modify cellular plan settings. The default setting is On. For supervised devices running iOS 11 (minimum version).
- Removing system apps: If this restriction is set to Off, users can’t remove system apps from their device. The default setting is On. For supervised devices running iOS 11 (minimum version).
- Setting up new nearby devices: If this restriction is set to Off, users can’t set up new nearby devices. The default setting is On. For supervised devices running iOS 11 (minimum version).
To configure those restrictions, go to Configure > Device Policies. For more information on setting restrictions, see Restrictions device policy.
Support for the new Cisco AnyConnect VPN client for iOS
Cisco is phasing out the Cisco AnyConnect client that was based on a now deprecated VPN framework. Cisco renamed that client to Cisco Legacy AnyConnect. The bundle ID is unchanged, com.cisco.anyconnect.gui.
Cisco has a new client named Cisco AnyConnect. The new client provides a more reliable connection to internal resources and support for UDP and TCP applications with per-app VPN. The bundle ID for the new client is com.cisco.anyconnect. Cisco supports the new client for iOS 10 (minimum version).
FileVault device encryption on enrolled macOS devices
The macOS FileVault Disk Encryption feature protects the system volume by encrypting its contents. With FileVault enabled on a macOS device, a user logs in with their account password each time that the device starts. If the user loses their password, a recovery key enables them to unlock the disk and reset their password.
The XenMobile device policy, FileVault, enables FileVault user setup screens and configures settings such as recovery keys. For more information about FileVault, see the Apple support article, https://support.apple.com/kb/PH25107.
Support for Samsung Enterprise Firmware-Over-The-Air
Samsung Enterprise FOTA (E-FOTA) lets you determine when devices get updated and the firmware version to use. E-FOTA enables you to test updates before deploying them, to ensure that the updates are compatible with your apps. You can force devices to update with the latest firmware version available, without requiring user interaction.
Samsung supports E-FOTA for Samsung KNOX 2.7.1 devices (minimum version) that are running authorized firmware.
Enhanced security for work profiles for Android for Work
Work profile passcode
For devices running Android 7.0 and later, you can now require a passcode for apps within a work profile for Android for Work. Users are prompted to enter the passcode when they attempt to open any apps in the work profile. When users enter the passcode, they can then access apps in the work profile. You configure a passcode requirement for the work profile only or for the device.
Default security policies
By default, the USB Debugging and Unknown Sources settings are disabled on a device when it is enrolled in Android for Work in work profile mode.
Other improvements
- New iOS Setup Assistant Option: New feature highlights. The iOS Setup Assistant item, New feature highlights, sets up these onboarding informational screens: Access the Dock from Anywhere and Switch Between Recent Apps. You can choose whether to omit those onboarding screens from iOS Setup Assistant steps when users start their devices the first time.
New Feature highlights is available for iOS 11.0 (minimum version). The default for all items is unselected. - Control OS Update device policy for macOS. You can now use the Control OS Update policy to deploy OS updates to macOS devices that are supervised or that are deployed through Apple DEP.
- Option to allow multiple users to use a Samsung SAFE device. The Restrictions device policy now includes the hardware control option, Allow multiple users. This option, for MDM 4.0 and later, defaults to OFF.
- Disable apps on Samsung SAFE devices. You can use the Restrictions device policy to block a list of installed apps from running on Samsung SAFE devices. By default, the new Disable Applications setting is Off, which means apps are enabled. To disable an installed app, change the setting to On, click Add in the Application List table, and then type the app package name.
- The Manage > Devices page now includes these additional device properties reported by Android devices:
Carrier Code (reported only by devices running Samsung MDM 5.7 or higher) Model Number (reported only by devices running Samsung MDM version 2.0 or higher) - Restrictions device policy now includes a policy to disable the camera on Android devices. To configure the policy, go to Configure > Device Policies, click Add, and click Restrictions. By default, camera use is enabled. To disable camera use, change the Camera setting to OFF.