
This blog post is cross posted on arnaudpain.com and tech-addict.fr, as we (Arnaud Pain and Samuel Legrand) have decided to work together to present this topic in mulitple events in 2019.
We have decided to work on this presentation to help users understand how they can rely on Azure for their data protection.
Here after some more information on the implementation and our feedback.
What is ADC and GSLB?
Citrix ADC on Azure vs On-premises
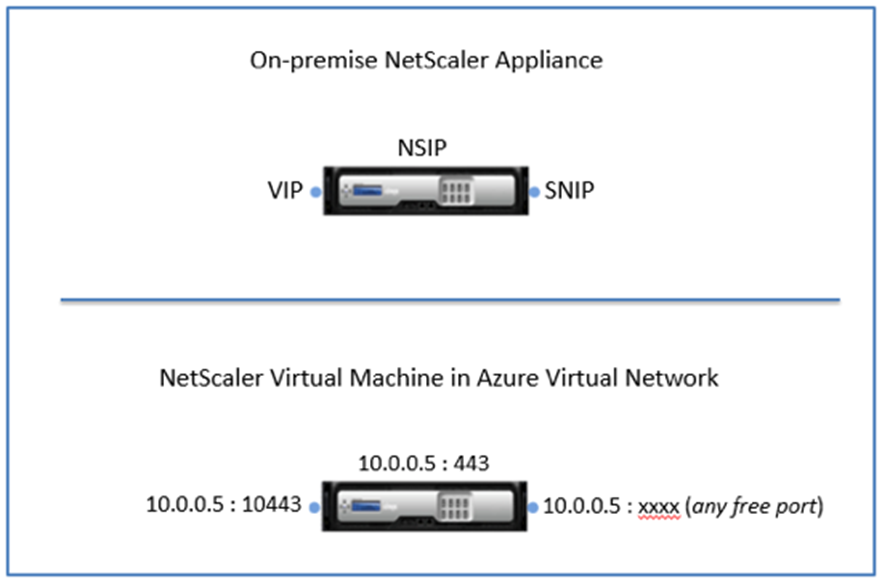
- In an on-premises deployment, a Citrix ADCVPX instance requires, at least three IP addresses:
- Management IP address called the Citrix ADC IP (NSIP)
- Subnet IP (SNIP) address for communicating with the server farm
- Vitual server IP (VIP) address for accepting client requests
- In an Azure deployment, only one IP address (a private (internal) address) is assigned to an instance during provisioning through DHCP.
Why ADC + GSLB on Azure and not Azure Traffic Manager?
Citrix ADC can be used in combination with GSLB feature to provide Business Continuity or Disaster Recovery for Citrix solutions but also to protect for example web sites.
Azure Deployment
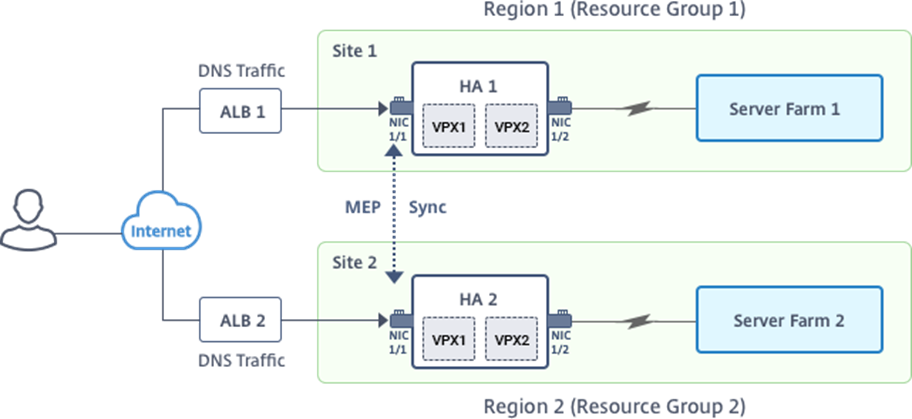
You can deploy Citrix ADC VPX instances on ARM either as standalone instances or as high availability pairs in active-active or active-standby modes.
In this scenario, each VM has three NICs – NIC 0/1, 1/1, and 1/2. The NICs are configured for the following purposes.
- NIC 0/1: to serve management traffic
- NIC 1/1: to serve client-side traffic
- NIC 1/2: to communicate with back-end servers
Our Lab
The following procedure is based on a Lab we used for our tests.
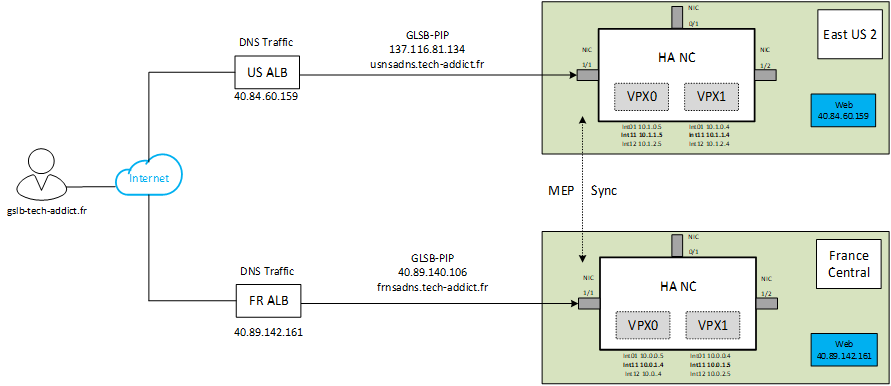
The Lab is composed of 2 Citrix ADC 13.0 in HA pair, 1 in US and 1 in France.
Behind those ADC we have a Web Server for the purpose of this Demo.
We will show you how to deploy and configure GSLB Active-Active configuration with static proximity.
Step-by-Step guide
ADC HA Pair deployment
Web Server Deployment
Reduce costs
By default our ADC HA pair is deployed using DS3 v2 instances for around $170 in East US 2 Azure resource location, changing to B2ms will help reduce costs to around $62.
Changing type from Premium SSD to Standard SSD will also help to reduce cost.
It can be interesting to change instance size and disk for Dev/Test, for production this will need validation to ensure to not impact the performance.
External Access to Citrix ADC
By default you will not be able to access ADC web portal, in fact only SSH port 22 is opened when Template is deployed.
You will need to add an inbound rules, in our case we will authorize SSL connection.
ADC Configuration
Now we can access our ADC using the public IP on SSL.
We will make the initial configuration which is basic:
- Install License
- Configure Load Balance Virtual Server for our internal Web Server
- Validate access to the web server
Reminder: GSLB Feature require Enterprise License
Azure GLSB PIP using Azure Web Portal
Azure GSLB PIP using PowerShell
If you want to use Azure PowerShell to create GSLB PIP, you will need first to provide some variable (to adjust based on your environment)
$locName=”East US 2”
$rgName=”CitrixADC”
$pubIPName4=”PIPFORGSLB1”
$domName4=”usvpxgslbdns”
$lbName=”alb”
$frontEndConfigName2=”FrontEndIP2”
$backendPoolName1=”bepool-11″
$lbRuleName2=”LBRuleGSLB1”
$lbRuleName3=”LBRuleGSLB2”
$lbRuleName4=”LBRuleDNS”
$healthProbeName=”probe-11”
After you will need to run the following command
$pip4=New-AzureRmPublicIpAddress -Name $pubIPName4 -ResourceGroupName $rgName -DomainNameLabel $domName4 -Location $locName -AllocationMethod Static
Get-AzureRmLoadBalancer -Name $lbName -ResourceGroupName $rgName | Add-AzureRmLoadBalancerFrontendIpConfig -Name $frontEndConfigName2 -PublicIpAddress $pip4 | Set-AzureRmLoadBalancer
$alb = get-AzureRmLoadBalancer -Name $lbName -ResourceGroupName $rgName
$frontendipconfig2=Get-AzureRmLoadBalancerFrontendIpConfig -LoadBalancer $alb -Name $frontEndConfigName2
$backendPool=Get-AzureRmLoadBalancerBackendAddressPoolConfig -LoadBalancer $alb -Name $backendPoolName1
$healthprobe=Get-AzureRmLoadBalancerProbeConfig -LoadBalancer $alb -Name $healthProbeName
$alb | Add-AzureRmLoadBalancerRuleConfig -Name $lbRuleName2 -BackendAddressPool $backendPool -FrontendIPConfiguration $frontendipconfig2 -Protocol “Tcp” -FrontendPort 3011 -BackendPort 3011 -Probe $healthprobe -EnableFloatingIP | Set-AzureRmLoadBalancer
$alb | Add-AzureRmLoadBalancerRuleConfig -Name $lbRuleName3 -BackendAddressPool $backendPool -FrontendIPConfiguration $frontendipconfig2 -Protocol “Tcp” -FrontendPort 3010 -BackendPort 3010 -Probe $healthprobe -EnableFloatingIP | Set-AzureRmLoadBalancer
$alb | Add-AzureRmLoadBalancerRuleConfig -Name $lbRuleName4 -BackendAddressPool $backendPool -FrontendIPConfiguration $frontendipconfig2 -Protocol “Udp” -FrontendPort 53 -BackendPort 53 -Probe $healthprobe -EnableFloatingIP | Set-AzureRmLoadBalancer
ADC GSLB Configuration
ADC GSLB Configuration using CLI
If you want to use Citrix ADC CLI to configure GSLB, you will need first to provide some variable (to adjust based on your environment):
enable ns feature LB GSLB
add service dnssvc 137.116.81.134 ADNS 53
add gslb site site1 40.89.140.106 -publicIP 40.89.140.106
add gslb site site2 137.116.81.134 -publicIP 137.116.81.134
add gslb service site1_gslb_http_svc1 40.89.142.161 HTTP 80 -publicIP 40.89.142.161 -publicPort 80 -siteName site1
add gslb service site2_gslb_http_svc1 52.179.142.180 HTTP 80 -publicIP 52.179.142.180 -publicPort 80 -siteName site2
add gslb vserver gslb_http_vip1 HTTP
bind gslb vserver gslb_http_vip1 -serviceName site1_gslb_http_svc1
bind gslb vserver gslb_http_vip1 -serviceName site2_gslb_http_svc1
bind gslb vserver gslb_http_vip1 -domainName gslb.tech-addict.fr -TTL 5
ADC GSLB Verification
Azure GSLB Rules
To have GSLB MEP works correctly we will need to create some rules to allow traffic between HA pair
ADC GSLB Validation
DNS Entries
You will need then to create DNS entries for GSLB to work correctly:
1 Global entry with type NS point to each Azure Resource Location Load Balancer Public IP
In our example:
- gslb.tech-addict.fr Type: NS Target: usnsadns.tech-addict.fr
- gslb.tech-addict.fr Type: NS Target: frnsadns.tech-addict.fr
2 entries with type A for each pointing to GSLB PIP:
- usnsadns.tech-addict.fr Type: A Target: 137.116.81.134
- frnsadns.tech-addict.fr Type: A Target: 40.89.140.106
DNS Validation
Configuration Validation
Test GSLB
Feedback and why to use Citrix ADC GSLB on Azure to be provided in a next article.
Stay tuned!