As I am working with Citrix Endpoint Management for few years now, I would like to see how Intune works.
I will share in articles my first steps to discover Intune. In this 1st one it will be initial configuration and enrollment of of device.
What is Microsoft Intune?
Intune is a cloud-based service in the enterprise mobility management (EMM) space that helps enable your workforce to be productive while keeping your corporate data protected. Similar to other Azure services, Microsoft Intune is available in the Azure portal. With Intune, you can:
- Manage the mobile devices and PCs your workforce uses to access company data.
- Manage the mobile apps your workforce uses.
- Protect your company information by helping to control the way your workforce accesses and shares it.
- Ensure devices and apps are compliant with company security requirements.
How does Intune work?
Intune is the component of Enterprise Mobility + Security (EMS) that manages mobile devices and apps. It integrates closely with other EMS components like Azure Active Directory (Azure AD) for identity and access control and Azure Information Protection for data protection. When you use it with Office 365, you can enable your workforce to be productive on all their devices, while keeping your organization’s information protected.

Microsoft Intune in the Azure portal
The Azure portal is where you can find the Microsoft Intune service.
Highlights of the Microsoft Intune experience in the Azure portal include:
- An integrated console for all your Enterprise Mobility + Security (EMS) components
- An HTML-based console built on web standards
- Microsoft Graph API support to automate many actions
- Azure Active Directory (AD) groups to provide compatibility across all your Azure applications
- Support for most modern web browsers
Let’s start
You will first need to connect to Office.

You need then to go in the Admin Portal

Click on Admin Center

Click on Intune

Click on Device Enrollment

As I do not have SCCM, I select Intune MDM Authority and click on Choose

To test with an Apple Device, click on Apple enrollment

Click on Apple MDM Push certificate

Select the box I agree and click on Download your CSR

When the CSR is downloaded, click on Create your MDM push Certificate

Connect with your credentials to Apple Push Certificates Portal

Click on Create a Certificate

Check the box and click on Accept

Click on Choose File

Select the CSR and click on Upload

Click on Download
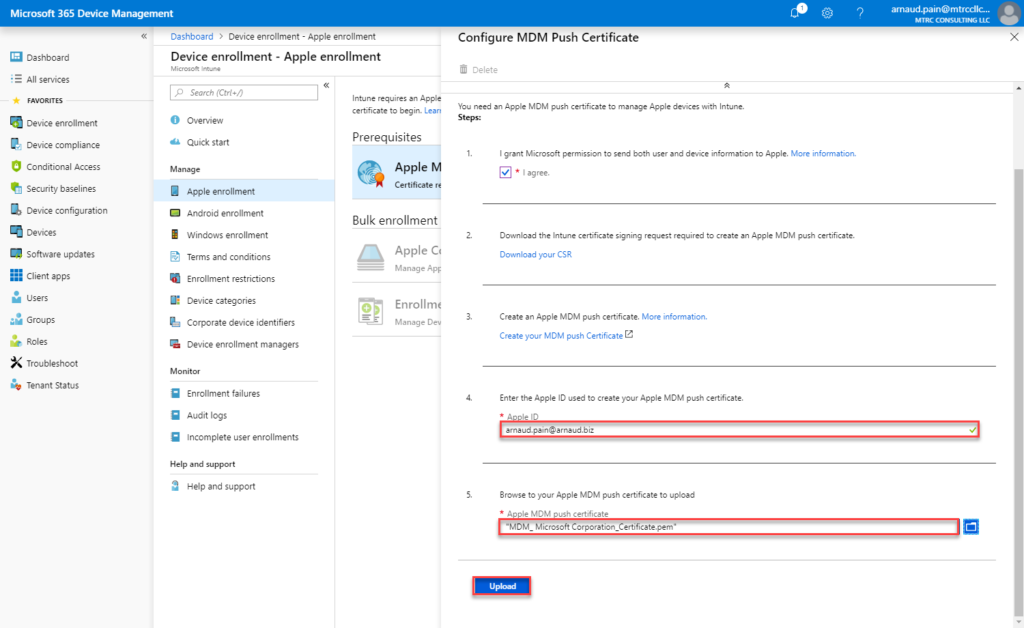
Provide the AppleID used to create your Apple MDM push certificate, select the .pem certificate downloaded from Apple Portal and click on Upload

When certificate is uploaded, click on the x sign in the top right corner
Prepare Intune
Here after we will see how to create device compliance policies with conditional access to make sure that iOS devices.
Create the iOS device compliance policy
Set up an Intune device compliance policy to set the conditions that a device must meet to be considered compliant. For this tutorial, we’ll create a device compliance policy for iOS devices. Compliance policies are platform-specific, so you need a separate compliance policy for each device platform you want to evaluate.
- In Intune, select Device compliance > Policies > Create Policy.

- In Name, enter iOS compliance policy
- In Description, enter iOS compliance policy test
- Under Platform, select iOS.

- Select Device Health. Next to Jailbroken devices, select Block, and then select OK.

- Select System Security and enter Password settings. For this tutorial, select the following recommended settings:
- For Require a password to unlock mobile devices, select Require.
- For Simple passwords, select Block.
- For Minimum password length, enter 4.
- For Required password type, choose Alphanumeric.
- For Maximum minutes after screen lock before password is required, choose Immediately.
- For Password expiration (days), enter 41.
- For Number of previous passwords to prevent reuse, enter 5.
- Select OK

- Select OK again

- Select Create

Create the conditional access policy
Now we’ll create a conditional access policy that requires all device platforms to enroll in Intune and comply with our Intune compliance policy.
Conditional access policies are configurable in either the Azure AD portal or the Intune portal. Since we’re already in the Intune portal, we’ll create the policy here.
- In Intune, select Conditional access > Policies > New policy.

- In Name, enter Device Compliance Policy.
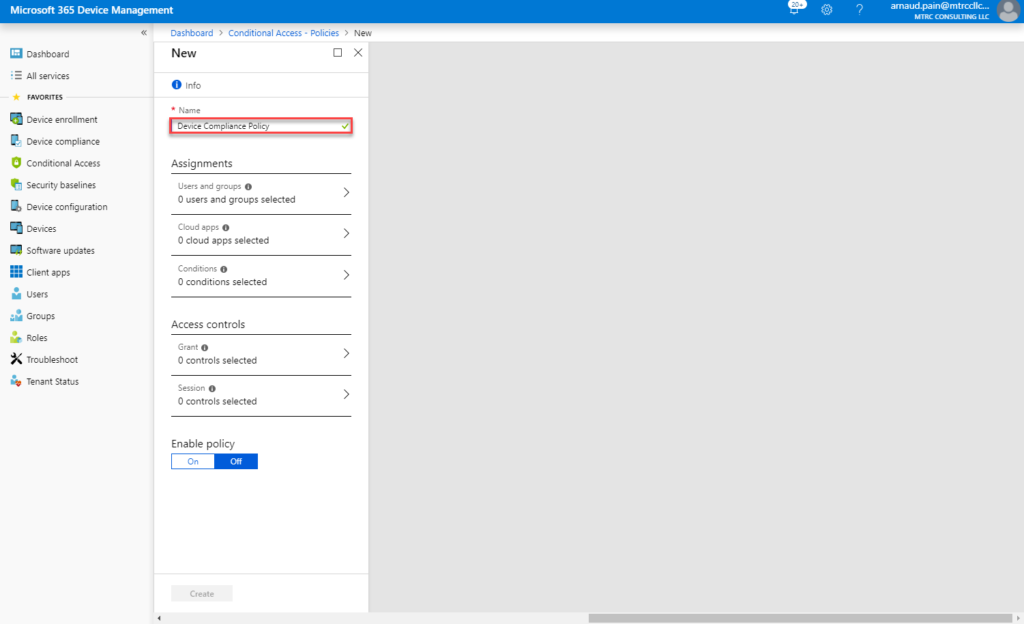
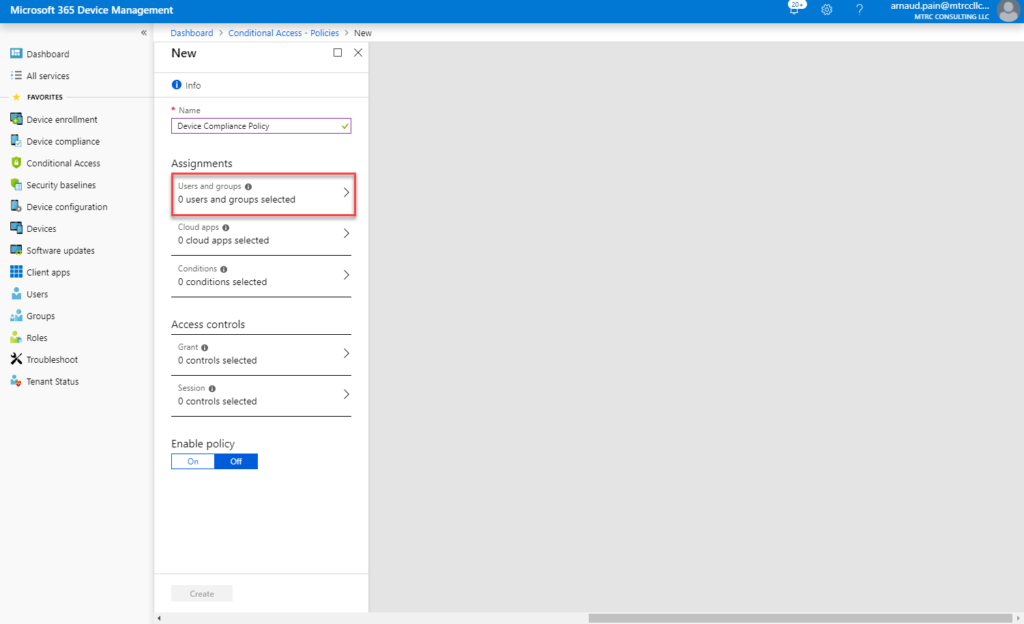
- Click on Assignments
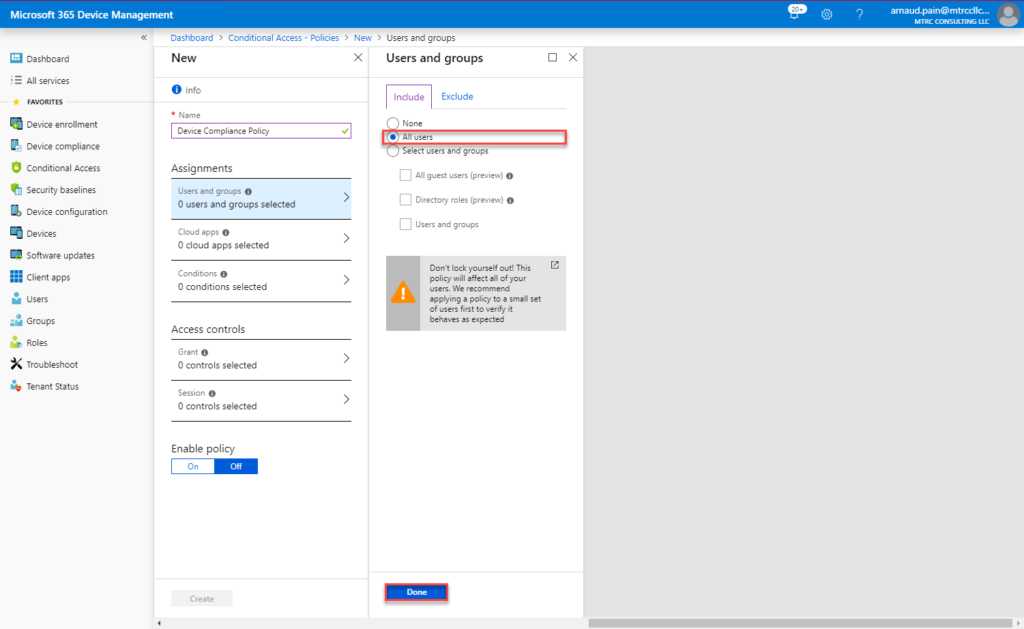
- Select Users and groups. On the Include tab, select All users, and then select Done.
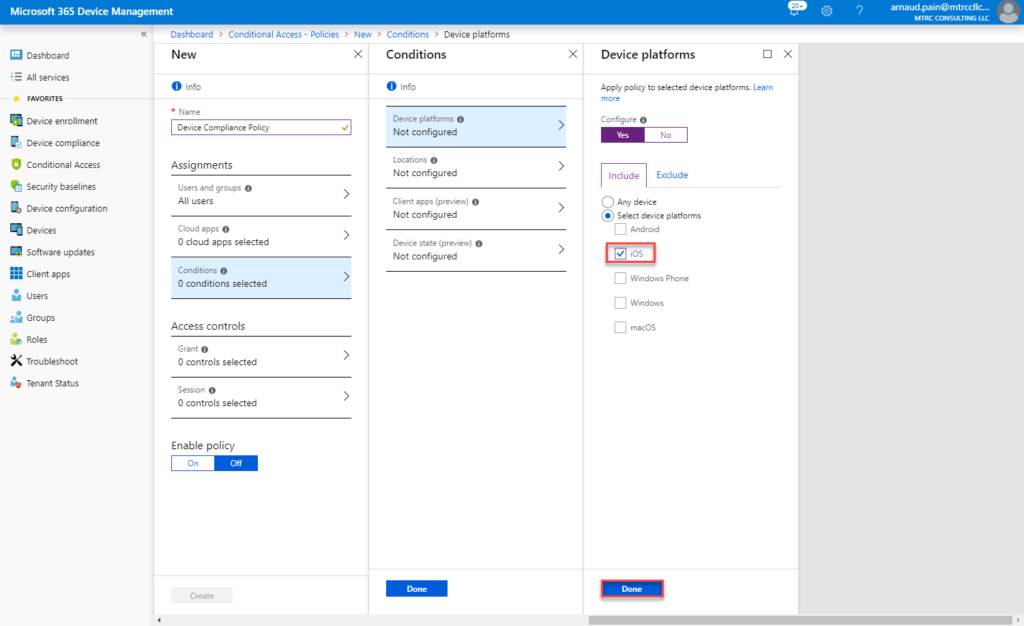
- Under Assignments, select Conditions > Device platforms.
- Under Configure, select Yes.
- On the Include tab, select iOS, and then select Done.
- Select Done again.
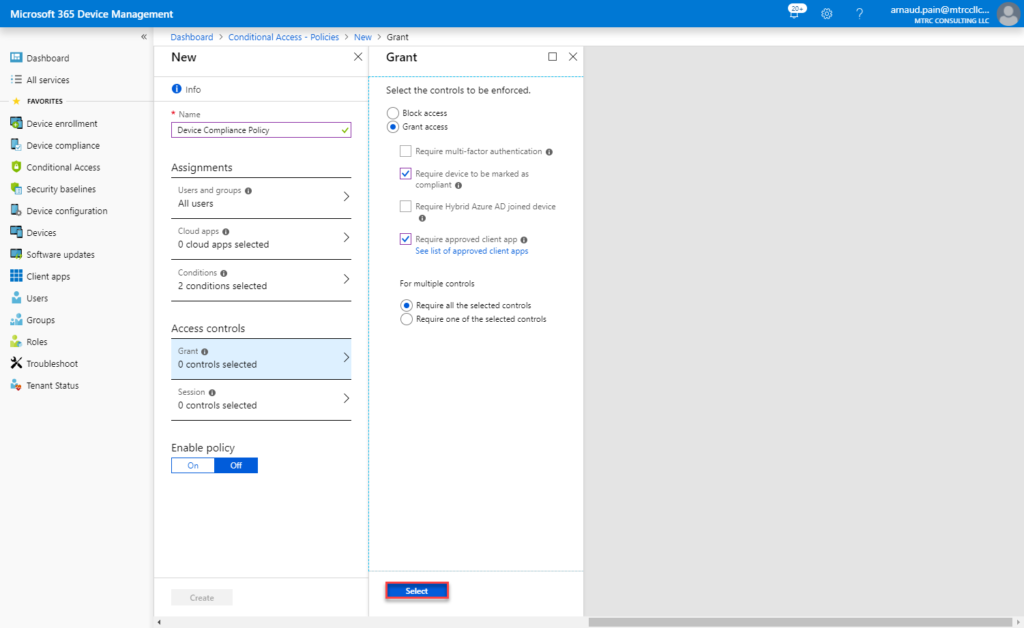
- Under Access controls, select Grant.
- On the Grant pane, select Grant access.
- Select Require device to be marked as compliant.
- Select Require approved client app.
- Under For multiple controls, select Require all the selected controls. This setting ensures that both requirements you selected are enforced when a device tries to access email.
- Choose Select.
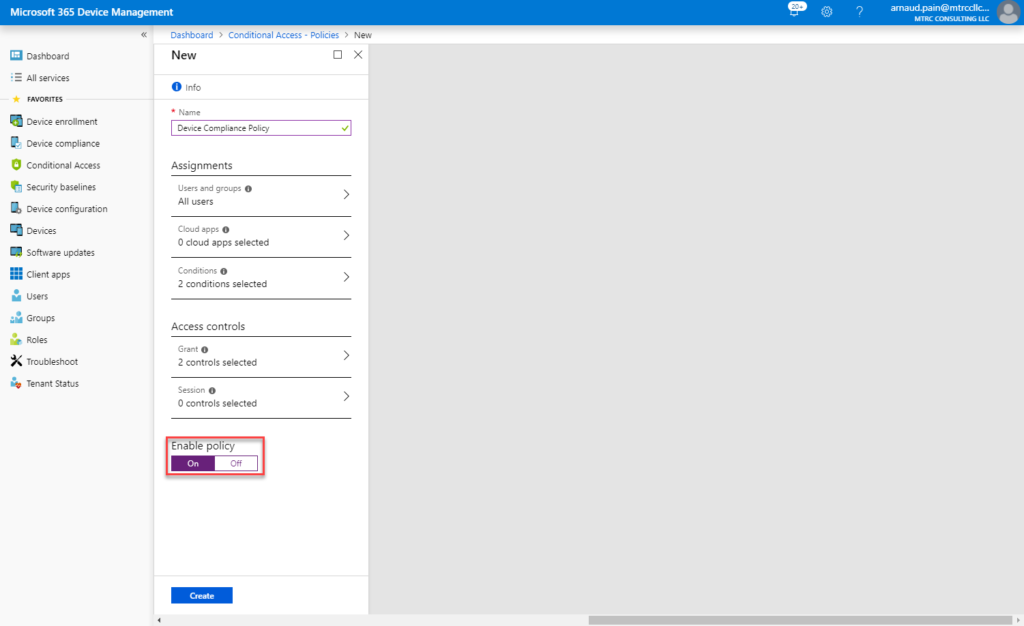
- Under Enable policy, select On.
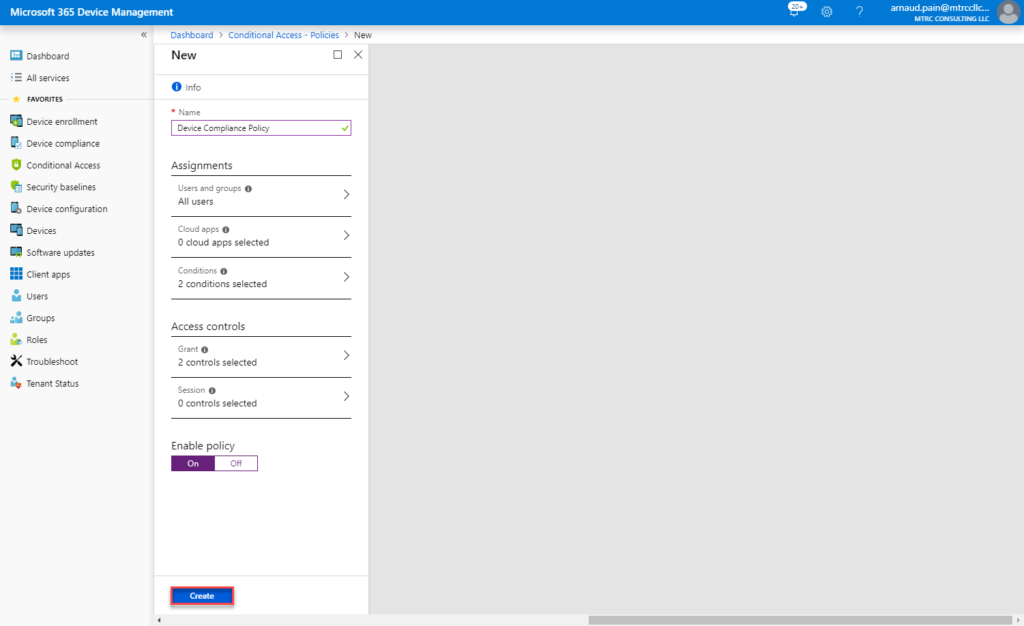
- Select Create.
Enroll a Device

- Open Store and download Intune Company Portal

- Once the Application is downloaded press OPEN
- Provide you email and press Go

- Provide your password and press Sign in

- Press Begin

- Press Continue

- Press Continue

- Press Allow

- Press Install

- Press Install

- Press Install

- Press Trust

- Press Done

- Press Open

- Press Done

- You’re presented with the above screen.

- We can see in Intune portal that device is enrolled and compliant.
In next article I will explain you step-by-step how to add and configure applications in Intune Store.
