If you have implemented Xenmobile solutions you probably have been asked or ask yourself how can the MAM part can be restrict.
I mean by default you can access the MAM portal, for example: https://mam.domain.com which can be access by a browser
It can be useful to check the XenMobile configuration as 404 is expected after successful authentication:
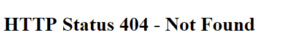
However this page is publicly available for different possible security attacks: XSS, SQL Injection, Brute Forcing, …
Here after are some steps to secure and restrict the MAM page:
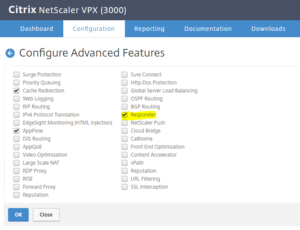
- Enable Responder feature on your NetScaler (under System / Settings / Configure Advanced Features)
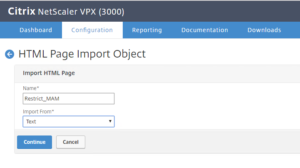
- Create a Responder HTML Page (under AppExpert / Responder / HTML Page Imports, click on Add). Provide a Name and select Import From: Text, click on Continue
- Then you can put HTML code, here after an example
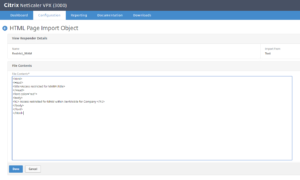
Click on Done
- Create a Responder Action (under AppExpert / Responder / Actions, click on Add). Provide a Name, select Type Respond with HTML Page, select the HTML Page previously created and click on Create
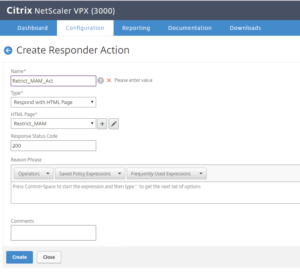
- Create a Responder Policy (under AppExpert / Responder / Policy, click on Add). Provide a Name for the Policy, select the Action previously created.
Under Expression, add the following:
HTTP.REQ.URL.EQ("/vpn/index.html")&& HTTP.REQ.HEADER("User-Agent").CONTAINS("Mozilla")
Click on Create

- Assign Responder Policy to the MAM NetScaler Gateway (under NetScaler Gateway / Virtual Servers, edit your XenMobile NetScaler Gateway)

- Click on the + sign
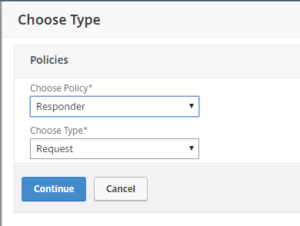
- Select Policy type Responder and click on Continue

- Select the Policy previously created and click on Bind

- Verify that the Responder Policy is bound and test
Now when a user will try to connect to https://mam.domain.com he will see the following screen:

It’s based on the HTML code I provided in this article and this can be changed.