How to implement the recommended protections and do it without impacting user productivity?
If you have Citrix XenMobile, you already have the means to effectively deal with ransomware. XenMobile has built-in features and secure mobile apps that can prevent these attacks from being successful.
In this post, I’ll share with you some details on how you can configure whitelists/ blacklists and other built-in features to prevent ransomware attacks and the chaos and expense they cause.
These policies, settings and automated actions can all be found under the “Configure” tab on the XenMobile Admin console.
To protect against ransomware — or any malware for that matter — you need to control access to ensure only authorized users can access cloud-based applications, encrypt sensitive data, and secure and control your data at rest and in transit. The XenMobile settings I will share go above just using, for example, the disable macro functionality in the Microsoft Office trust center. With a combination of policies and automated actions, XenMobile Server allows you to whitelist good sites, blacklist known bad sites (which you should continually update based on suspicious traffic), lock down user accounts, and prevent writing to system files and settings.
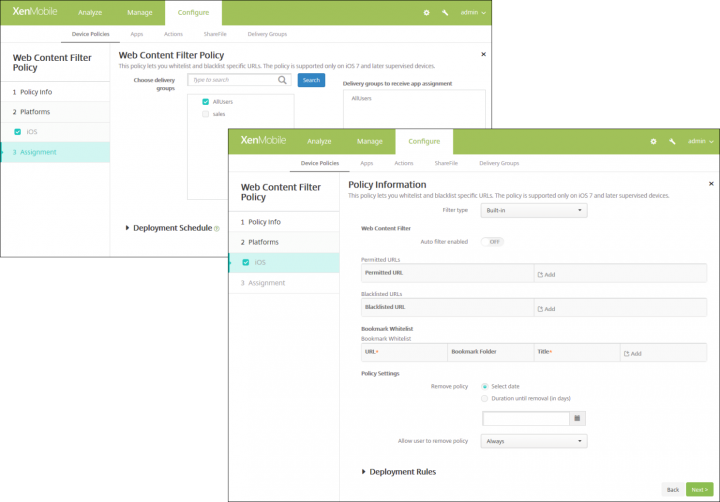
Managing white and black lists for URLs can be bothersome. And you won’t know about a ransomware attack until you get infected, but once you do, and analyze the infection, you can use a XenMobile Web Content Filter Device Policy as an incident response tool to block the specific domain used for the ransomware CNC. For example, you could add a policy filter web content on iOS devices leveraging Apple’s auto-filter function in conjunction with specific sites that you add to whitelists and blacklists.
You can also leverage SmartControl, a new Citrix technology available in NetScaler with Unified Gateway to provide contextual security across usage situations and device configurations. Using SmartControl, policies are enforced to perform and enable many tasks including configuring per-application MicroVPNs for Citrix XenMobile users to encrypt and protect mobile applications with specific network functions
Another XenMobile capability is the flexibility built into the Managed Domains Device Policy, so you can lock down business accounts while leaving personal accounts alone. For iOS devices for example, you can define managed domains that apply to email and the Safari browser. Managed domains help you protect corporate data by controlling which apps can open documents downloaded from domains using Safari. When a user sends email to a recipient whose domain is not on the managed email domains list, the message is flagged on the user’s device to warn them that they are sending a message to someone outside your corporate domain.
For items such as documents, attachments, or downloads: when a user opens an item using Safari from a web domain that is on the managed web domains list, the appropriate corporate app opens the item. If the item is not from a web domain on the managed web domains list, the user cannot open the item with a corporate app. They must use a personal, unmanaged app.
For supervised, or corporate-owned, devices, even if you do not specify Safari password autofill domains: If the device is configured as ephemeral multi-user, users can’t save passwords.
With the Restrictions Device Policy, you can allow or restrict certain features or functionality on user devices, such as the camera. You can also set security restrictions, as well as restrictions on media content and restrictions on the types of apps users can and cannot install. Most of the restriction settings default to ON, or allows.
The Apps Restrictions Policy allows you to create blacklists for apps you want to prevent users from installing on Samsung KNOX devices. You can also create whitelists for apps you want to allow users to install.
Maybe the simplest solution is not technology at all — Education
Educating your users is a necessity and an important opportunity to eliminate the user errors that make these attacks possible. Ransomware and malware attacks will continue to put your company at risk, as long as your users are unaware and uneducated about the risks of the internet.
So, regularly talk to your employees (including upper management and IT staff) about cybersecurity. Encourage their cooperation, not just compliance. Cybersecurity training should be part of your general onboarding activities, and these trainings should include specific rules for email, web browsing, mobile devices and social networks.
Summary
Nothing is 100 percent effective, but the combination of XenMobile and user education can get it pretty close. With your data, time, effort, investment and even your company at stake, any reduction in the number of threats can contribute to an improved security posture. Take a look at your XenMobile deployment today and see what training and policy changes will work best for you.
Need more information about Citrix XenMobile? Here after you will find a range of resources, documentation, training and support for XenMobile deployment.
- XenMobile Resources
- XenMobile Documentation
- XenMobile Training from Citrix Education
- XenMobile Support
It’s easy to get started with XenMobile – no cost, no commitments
