Secure Mail currently supports certificate-based authentication (also referred to as client-based authentication) with on-prem Exchange Server environments.
A limitation with Office 365 deployments, however, made this feature unavailable to Office 365 users — until now. Microsoft recently announced certificate-based authentication support for users of Office 365 enterprise, business, education, and government plans. With this support, Secure Mail users with iOS and Android devices can finally take advantage of certificate-based authentication when connecting to Office 365.
Here is a high-level integration diagram of the various components involved in Certificate-Based Authentication.
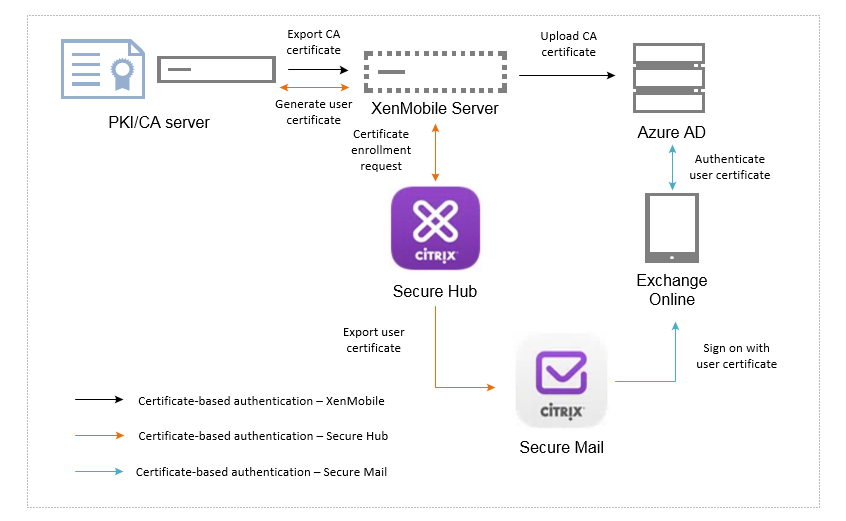
What is certificate-based authentication? How does it help Secure Mail users?
With certificate-based authentication, getting started with Secure Mail is super easy. Users authenticate by using a client certificate, instead of typing their credentials when they sign on to Secure Mail. They can open their mail automatically.
How do you enable certificate-based authentication in Secure Mail?
To make sure certificate-based authentication works with Office 365, you need to enable the feature in the XenMobile console, Exchange online, Azure Active Directory (AD), and Active Directory Federation Services (ADFS) on Windows Server. Support for certificate-based authentication in Secure Mail already exists for on-premise Exchange configurations. So, if you had already set it up, users with Secure Mail versions 10 and later can take advantage of certificate-based authentication to connect to their Office 365 accounts. If you haven’t set it up yet, see http://docs.citrix.com/en-us/xenmobile/server/authentication/client-certificate.html
Prerequisites
- A federation server with Azure Active Directory (AD).
- A copy of the certificate (X.509) generated from the CA server when configuring PKI with XenMobile Server.
- The CA must have a certificate revocation list (CRL) that can be referenced via an Internet-facing URL.
- The RFC822 Name or the Principal Name value in the certificate Subject Alternative Name field must have the user’s email address.
Basic Steps
- To enable certificate-based authentication in XenMobile Server for the first time, see http://docs.citrix.com/en-us/xenmobile/server/authentication/client-certificate.html.
- Enable modern authentication in Exchange Online. Modify the default login behavior of Azure AD to enable certificate authentication.
- Upload the public portion of the certificate (X.509) to Azure AD. Modify the primary authentication method in ADFS to include Certificate Authentication. For Azure AD to revoke a client certificate, add the certificate Serial Number and Issuer claims in ADFS.
For step-by-step instructions on the configuration, refer to the Product Documentation site: http://docs.citrix.com/en-us/xenmobile-apps/10/secure-mail/certificate-based-authentication-office365.html